Technology
The Digital Postal Service
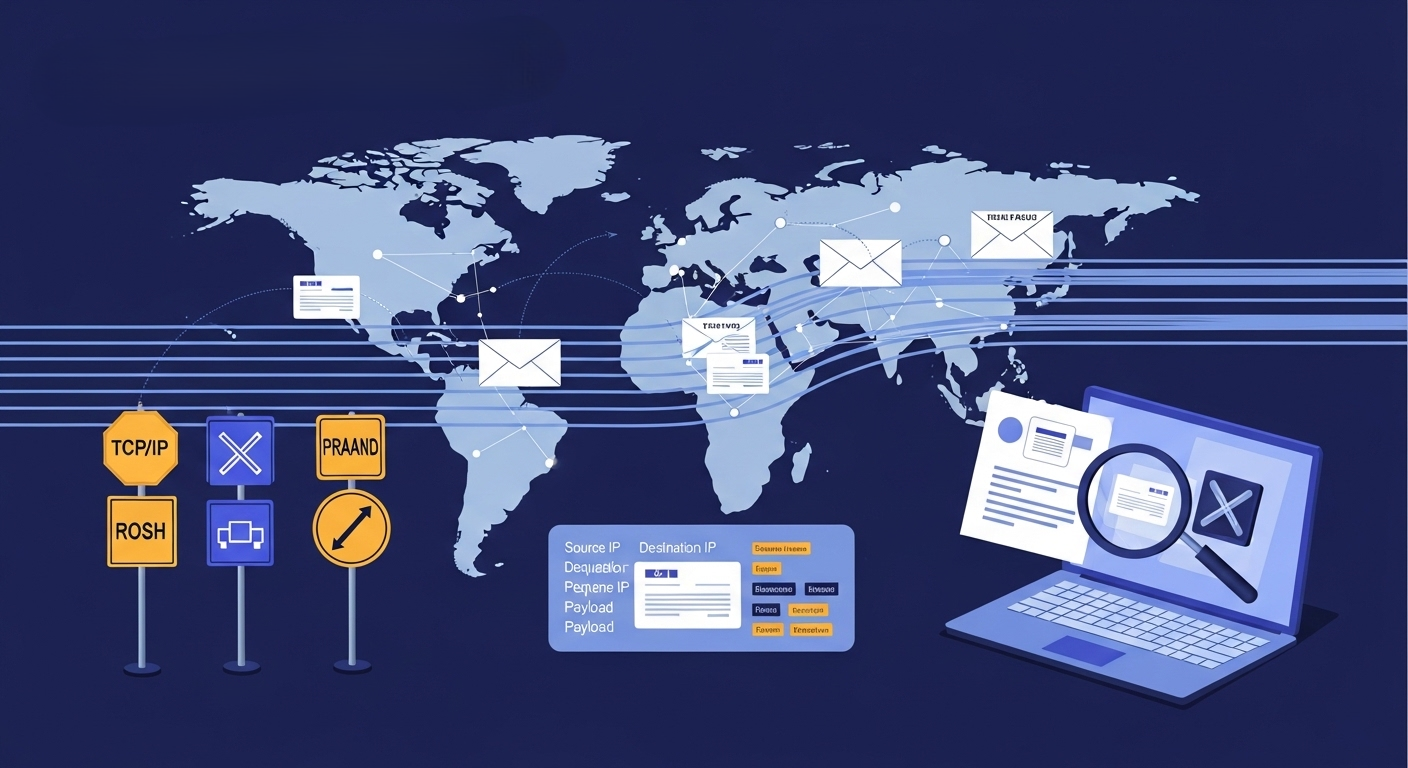
Network Protocols and Packet Analysis
It seems as an incessant stream of information when sending an email or watching a video. The internet is in fact, more of a huge, disorderly postal service. Your information is not teleported, it is broken in small fragments, labeled and transported over a thousand miles of fibre.
To get a clear picture of the inner mechanisms of internet functioning (and how to troubleshoot it once it malfunctions), we must be aware of the rules of the road ( Protocols ) and the vehicles that transport the data (Packets).
1. The Rules - Network Protocols
A Protocol is nothing more but a collection of established rules of communication. It’s like a language. When I am talking English and you are speaking French, we cannot share ideas. We need a shared protocol.
All the internet operates on these protocols which were stacked together to form what is commonly referred to as the TCP/IP suite.
-
IP (Internet Protocol) The Addressing System. Each device possesses an IP address (similar to house address). It has the role of transferring the data between Computer A and Computer B.
-
TCP (Transmission Control Protocol) Reliability Manager. It makes sure that the information reaches where it is supposed to be and, everything is in place. In case of any lost piece, TCP requests a resentment.
-
HTTP/DNS The Application Layer. These are the languages that your browser speaks to request the websites (HTTP) or search domain names (DNS).
2. The Vehicle - What is a Packet?
In the case that you wanted to transfer a 1GB file of movies to your friend, the network cannot send it in one block, it would congest the lines. Rather, the computer splits such file into thousands of minuscule bits named Packets.
Consider a packet to be a digital envelope. It has two main parts,
- The Metadata - The metadata is stored in the Header (The Envelope Info). Who sent it (Source IP)? Whither to (Destination IP)? What number packet is it (Sequence Number)?
- The Payload (The Content) - The actual piece of data (a chunk of the movie file, or of the text of an email).
After delivery of the packets to the receiver, the computer receiving the packets removes the headers and restores the parts of the payload into the initial file.
3. The X-Ray - Packet Analysis
Then, when things go wrong what happens? Slow internet connection, or are you even sure that you are being hacked? You have to see what is in the envelopes. This is Packet Analysis (or "Sniffing").
Prostitution tools such as Wireshark are employed by network engineers to capture and read these packets in real-time.
- Bugging - The reason behind this slow-loading site? The packets allow an analyst to determine whether the server is responding too slowly (High Latency) or packets are being lost in transit (Packet Loss).
- Security - "Is my network infected with malware? Security experts seek after suspicious packets. As an example, when your smart thermostat starts transmitting packets to an unfamiliar server in the other country, this is indicative of a red flag.
In summary
The Invisible Flow. The internet may appear like magic, yet it is an extremely sophisticated structure of regulations and logistics. Knowing protocols and packets provides an X-Ray knowledge. It makes the invisible stream of data measurable, analyzable and obtainable.
Test Your Knowledge!
Click the button below to generate an AI-powered quiz based on this article.
Did you enjoy this article?
Show your appreciation by giving it a like!
Conversation (0)
Cite This Article
Generating...

.png)